


Manufacturing Use Case: Protecting B2B2C

▶ Over 60% of breaches are caused by third-party providers
▶ Sharing ERP data amongst partners has risks
▶ Mimecast, “Manuf. Industry endured ~24M spam attacks”
▶ Zero trust data-protection for a secure supply-chain

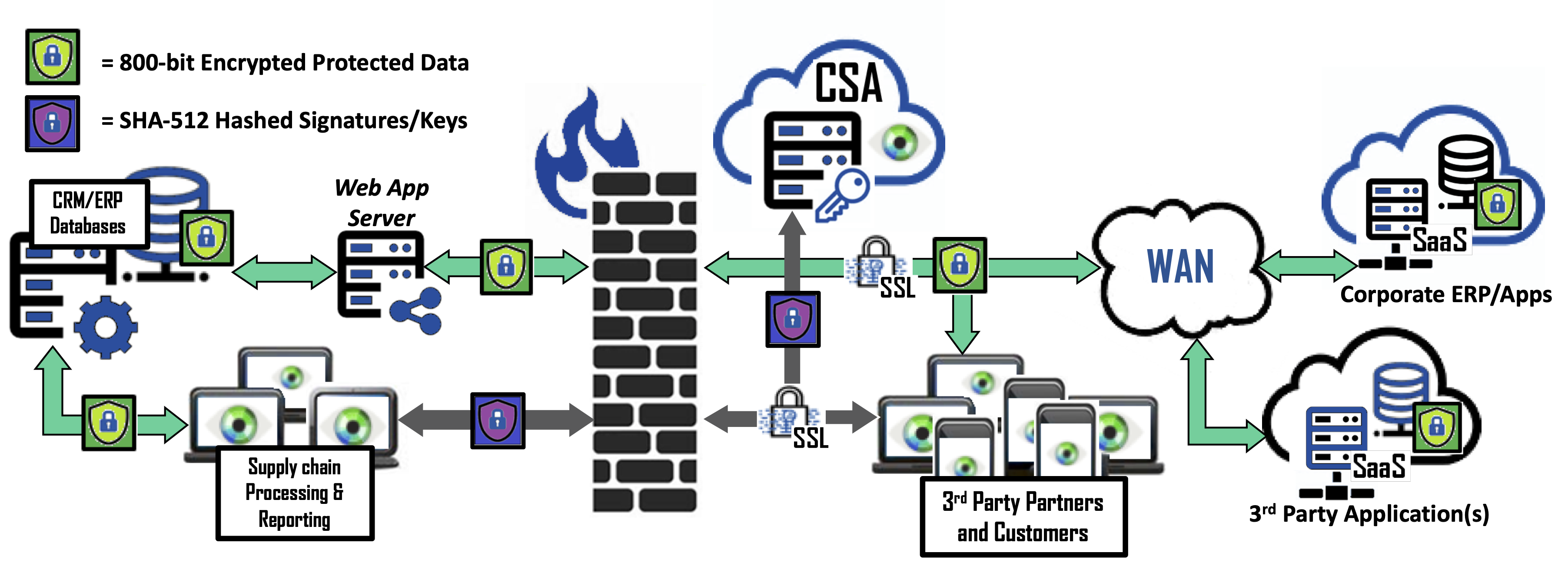
The backbone for the Manufacturing industry’s supply chain is the Enterprise Resource Planning (ERP) systems and the databases they contain. ERP systems have evolved to cloud based SaaS solutions that are highly integrated with CRM, MES, MRP, Financial and HR systems, opening a potential gateway for thieves to steal sensitive data about customers and/or employees. Bonafeyed’s Data Defined Security protects this critical data whether on-premises, on the third-party’s premises or in cloud base application. Data protection with diversified encryption can control access on a per record basis or between a manufacture and specific third party. In all cases, the data remains secure even as it moves between network domains and on customers and suppliers end-point devices.
READ MORE:
Now more than ever, manufacturing supply chains needs protection, and the ability to receive and supply sensitive information to many different enterprises. From vendors to partners, these digital touch points allow for more efficient and effective operations. In a supply chain attack, a hacker will gain access to a partner or provider that has systems and data access. Through this relationship, the criminals can enter networks, steal data, and cause significant business harm. Bonafeyed demonetizes this shared data and prevents unauthorized access to supply chain data.


