



The underlying problem with data protection is a general lack of awareness and understanding of how to protect the data itself, not just guard the systems holding it. Data protection regulations do not specify how to safeguard data, only that “somewhere” encryption be utilized. Transit protection only secures data “in-flight”. Data “at-rest” protection only secures where data is physically stored. Traditional security solutions try to detect and prevent unauthorized access at the edge of an enterprise, but once a cybercriminal penetrates the security perimeter, data is freely available by querying the databases. When protected by Cy4Secure, unauthorized users can only receive or pilfer encrypted data. Data remains safe even while IT applies patches and updates to fix regularly discovered exploits to the perimeter security. In the event Cy4Secure protected data is lost, stolen, abandoned, or forgotten, it remains secure and is demonetized and permanently inaccessible once the crypto keys protecting it are disabled or retired, ensuring cybercriminals or non-authorized users only obtain unintelligible encrypted data.
Cy4Secure Data Security can be seamlessly and rapidly deployed in existing environments. All modern database systems can be protected without impacting user workflows, changing existing infrastructure, and with no perceivable impact to performance. Users or external customer/clients perform password-less or multi-factor authentication to validate credentials which allow access to protected data. More importantly, each data element or field can be independently encrypted/protected. No two data elements are required to share the same key or authorization requirements. Bonafeyed delivers privacy in plain sight!
Cy4Secure is Bonafeyed’s answer to the increasing threat of data breaches. Cy4Secure‘s architecture accomplishes this feat by only encrypting/decrypting data at authorized user endpoints. Our Data-Defined Security approach continuously safeguards data as it moves across different security domains, when it lands on an application server, after delivery from a cloud-based application, and finally, when the data rests on a recipient’s endpoint device. Cy4Secure uses the following security methods:
- Bonafeyed never sees or touches any customer data
- All encrypt/decrypt operations are performed on the user’s secure endpoint device (SED)
- All authentication data is hashed using SHA-512
- Shared data is encrypted before it leaves the user’s SED
- Encryption secrets are disassociated from the protected data’s location
- Data and corresponding encryption secrets only unite on an authorized user’s SED
- Agnostic Data-Defined Architecture with all transport, network, or other security protocols
- “Airgap” technology ensures keys and credential information are inaccessible to hackers
- Minimum of 800-bit size keys are utilized for strong crypto operations
- Five 9’s Availability for authentication, and crypto management services reliability and uptime
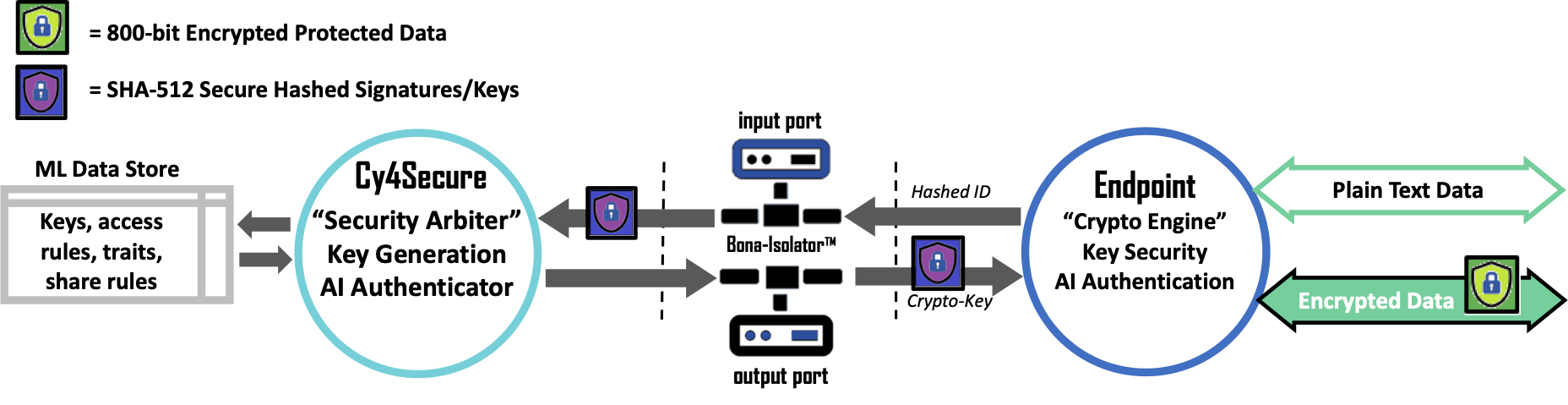
At the center of Bonafeyed’s data security is the Cy4Secure Arbiter (CSA) which is responsible for managing all crypto functions. They include maintaining crypto secrets and credentials relationship, authorizing crypto information, supporting RESTful API, enforcing encryption key lifecycles, monitoring access habits, trends, frequency to proactively detect attacks, and theft or misuse of user credentials. It stores cryptography secrets and credentials, operates in a highly reliable and available clustered and distributed configuration. The CSA is deployable within the cloud as a service or on premise using a software-defined deployment model.
The Bona-Isolator™ provides an industry leading security air gap between public facing servers and the CSA. It ensures that no direct access to the ML Data Store or the CSA is possible
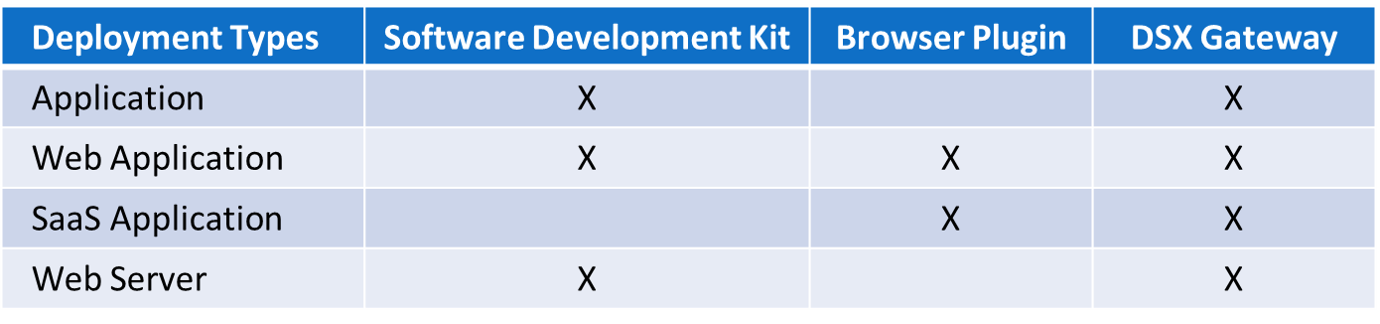
The Cy4Secure SDK allows easy cryptography integration into browsers, 3rd party SaaS, and Enterprise applications for automatic deployment to endpoint devices. The SDK provides prebuilt functions to perform cryptographic operations and to interact with the CSA. It also provides an optional conversion function to make encrypted data transportable across 8-bit transport mechanisms. The SDK supports multiple languages: JavaScript, Java, C, Python, C#, and Swift.

The Data Security Gateway (DSX) is a data gateway and security software that connects legacy devices and applications to Bonafeyed protected databases whether located in the cloud, within a SaaS product, or an on-premises DBMS. The DSX compliments existing security infrastructure and operates on application data independent of a protocol or data structure. Without any changes to end-point devices, DSX brings Bonafeyed’s data-defined security, data cryptography, and last mile protection - a rapid, light-weight deployment option for any Enterprise.
DSX is designed to interoperate with database management systems, database driven applications and 3rd party SaaS such as salesforce.com, Facebook Workplace, ServiceNow, and NetSuite. There is no change to an application’s functionality. Users continue transparent use of applications. DSX identifies and secures an application’s data so that the data is protected from hackers and cyber-thieves while allowing authorized users to see and use the protected data. It supports both the patented 800-bit high performance Stream Cipher and standard AES256 Block Cipher operations to protect data without impacting performance or functionality.
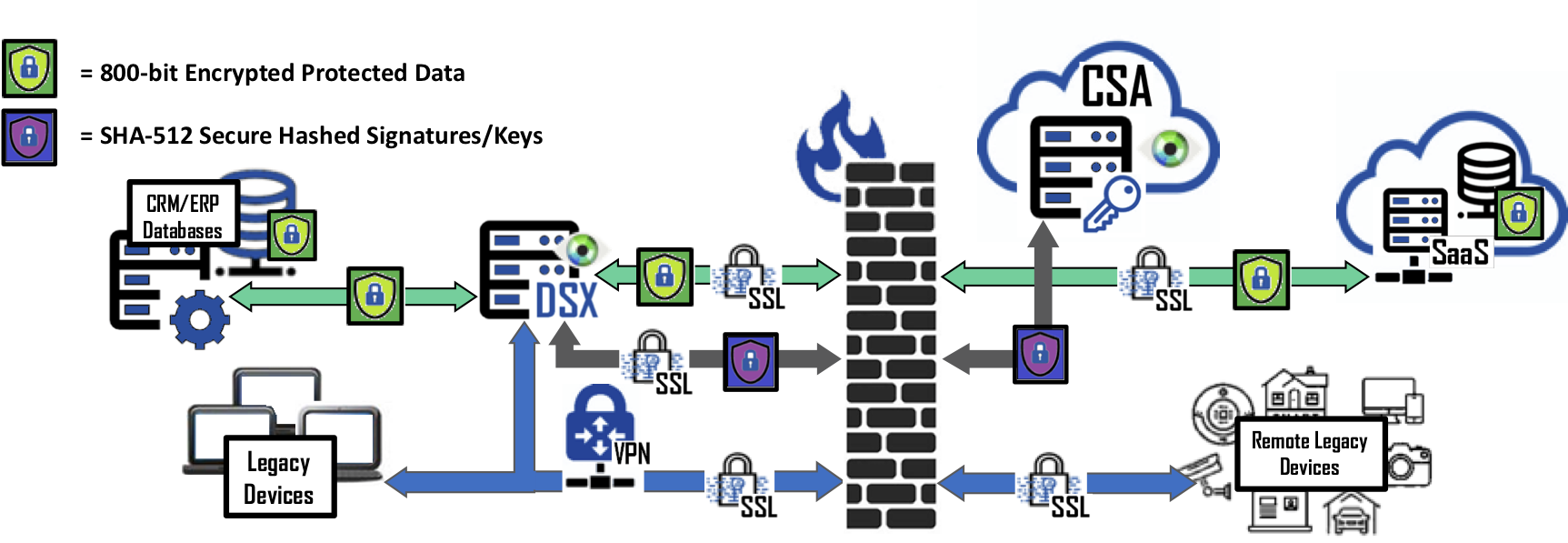
DSX encrypts application data fields before it is stored in the cloud and decrypts the data when it is en route to the client’s web application. The cloud applications or servers are not negatively impacted – it has no idea that the data is encrypted. Additionally, when the cloud server is hacked and the data stolen, the hackers only have access to encrypted data, digital gibberish. IT installs DSX on virtual machines or appliances, describes the cloud system, updates the configuration so DSX exists between the clients and application server, and DSX does the rest.
DSX performs encrypt/decrypt operations and works in conjunction with Bonafeyed’s Cy4Secure Arbiter (CSA) where users are authorized, and 800-bit encryption keys are created and managed. Each DSX supports up to 175 users and each cluster can manage up to 3 separate applications.
Key DSX features:
- Secured data gateway for any legacy and 3rd party SaaS applications
- Encrypts and Decrypts data between application servers and clients
- 800-bit or AES256 encryption, auto data field detection, and admin dashboard
- Supports 175 users per DSX node and up to 3 applications per DSX cluster
- High availability active-active n+m cluster failover design
- Low-latency, scalable high throughput architecture

Bonafeyed’s software development kit, SDK, natively supports data encryption within an application created and supported by a developer. It contains a very lightweight no latency encryption function using an 800-bit security algorithm or optionally AES-256 for cipher encoding/decoding. With only two code line additions, the SDK easily integrates into Javascript, C++, Java, or Python based applications to perform in-line data encryption/decryption operations transparently and seamlessly.
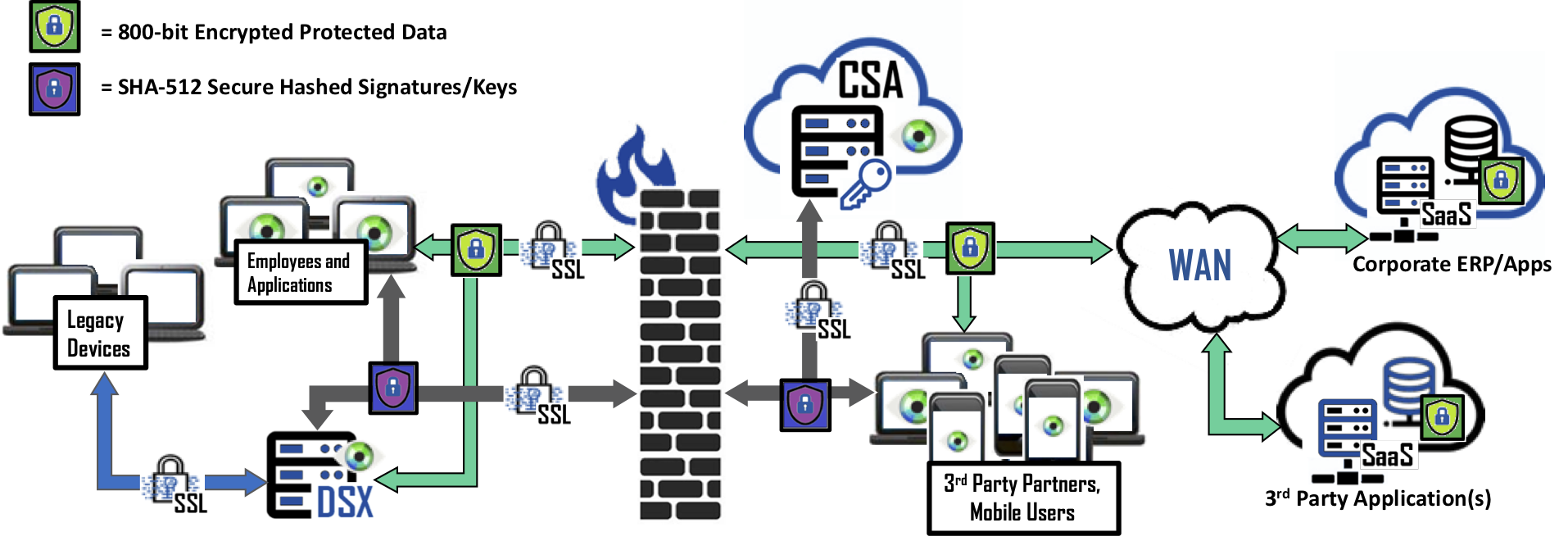
Applications that utilize off the shelf web browsers including Microsoft Windows Edge, Firefox, Google Chrome, and MacOS Safari are supported through a plugin. When data is sent or received, the plugin verifies a user’s permission to use the built-in cryptographic engine to either decrypt or protect data. In addition, the Data Security Gateway (DSX) facilitates the fastest deployment option for legacy devices or applications without the need for endpoint plugins or altering applications.
No matter the endpoint device, whether within the same network domain or external, the Cy4Secure system can extend the data security domain, validate and authorize access to protected data using an 800-bit Stream Cipher based technology. When encrypted data is lost, stolen, abandoned or forgotten, it remains protected and becomes permanently inaccessible or demonetized once access is deleted or retired ensuring cyber criminals or internal non-authorized users only obtain unintelligible data.


