


Data protection begins at the client’s computer system regardless of device type for the secure use of native applications, web browser applications or internet pages. This means data is protected before it leaves an endpoint device or network element and remains secure until the recipients of the data are authenticated to read or use the encrypted data. The Cy4Secure data protection system allows 100% Transparent “No-Touch” enterprise deployments or client “one-touch” 3rd-party application integration. A typical enterprise deployment entails an IT organization or resource to first determine the best deployment option for their applications. Depending on the application type the following options are possible for IT.
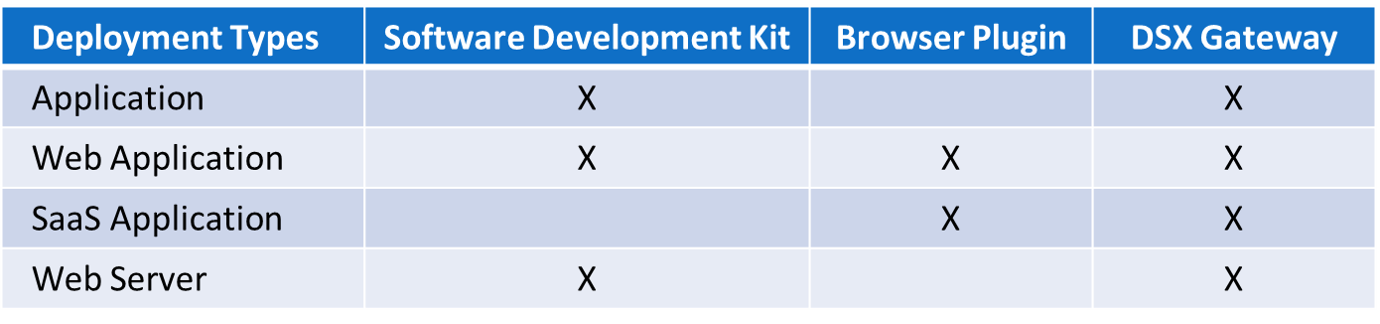
Bonafeyed’s software development kit, SDK, natively supports data encryption within an application created and supported by a developer. It contains a very lightweight no latency encryption function using an 800-bit security algorithm or optionally AES-256 for cipher encoding/decoding. With only two code line additions, the SDK easily integrates into Javascript, C++, Java, or Python based applications to perform in-line data encryption/decryption operations transparently and seamlessly.
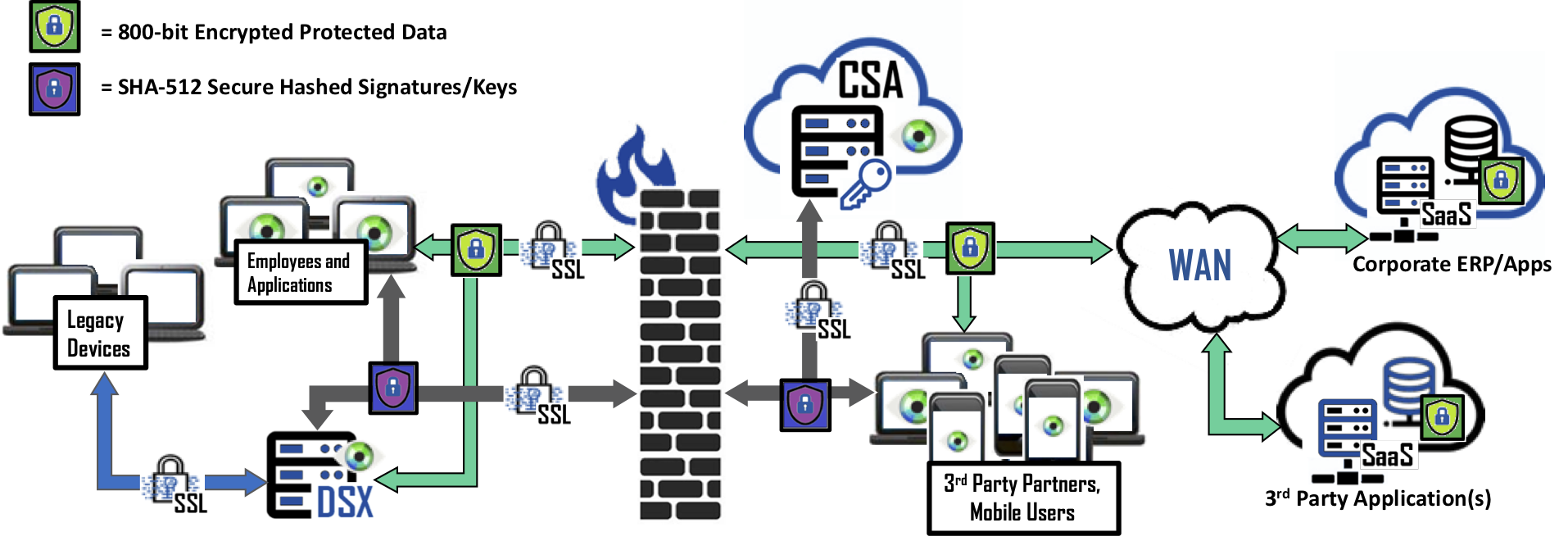
Applications that utilize off the shelf web browsers including Microsoft Windows Edge, Firefox, Google Chrome, and MacOS Safari are supported through a plugin. When data is sent or received, the plugin verifies a user’s permission to use the built-in cryptographic engine to either decrypt or protect data. In addition, the Data Security Gateway (DSX) facilitates the fastest deployment option for legacy devices or applications without the need for endpoint plugins or altering applications.
No matter the endpoint device, whether within the same network domain or external, the Cy4Secure system can extend the data security domain, validate and authorize access to protected data using an 800-bit Stream Cipher based technology. When encrypted data is lost, stolen, abandoned or forgotten, it remains protected and becomes permanently inaccessible or demonetized once access is deleted or retired ensuring cyber criminals or internal non-authorized users only obtain unintelligible data.


