▶ Databases are half of the “Double Extortion” schemes
▶ 250K MySQL DBs for sale from 85K victims
▶ 2021 Cybercrime damages predicted to reach $6 trillion
▶ Encrypting data in a Database demonetizes its value

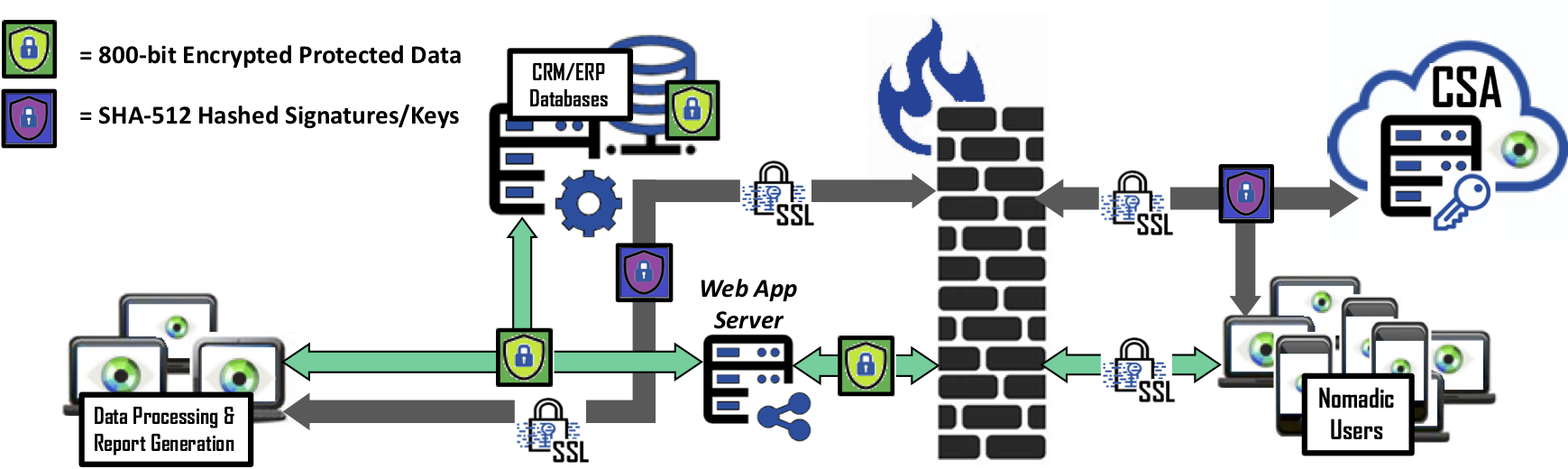
Bonafeyed’s Data-Defined protection approach – safeguards database entries rather than applying an “at-rest” encryption of the entire database or the storage where it resides. This means first encrypting data and then submitting to the database application. By leveraging this approach, the Cy4Secure data security solution is capable of individually encrypting each field or row or column of data. The benefits of protecting the records or individual fields allow not only the highest level of data protection but access control as well as preserving the value of the data.
The question that instantly comes to mind is, how can the database work with encrypted data? The answer is remarkably simple. Database systems do not know the difference between data that is encrypted with Cy4Secure or data that is human readable. Its only concern is that the data meets the entry field’s attributes. If it looks like data, databases can perform their operations such as whole searches and partial searches or sorts. When making queries, the operations are performed using Cy4Secure encrypted versions of the data and the database just searches for the encrypted equivalent version of the data. For instances where arithmetic operations are required on numerical entries, order preserving encryption can be used on numerical fields. Conversely, each PII numeric data entries such as a social security numbers, can be individually encrypted and obfuscated because they are not used in mathematical or sorting operations.
Therefore, individual data fields, records and columns can be encrypted to control access from unauthorized users. This allows broader sharing of its data or records and ensures in the event of a data breach or theft by a bad actor, data remains protected, unavailable, and demonetized.